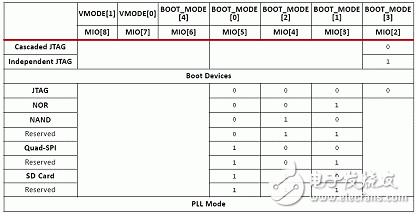
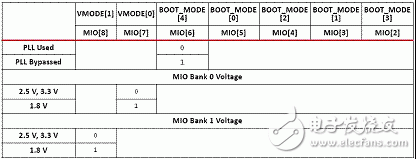
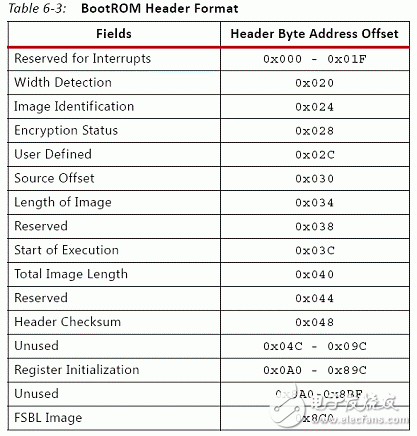
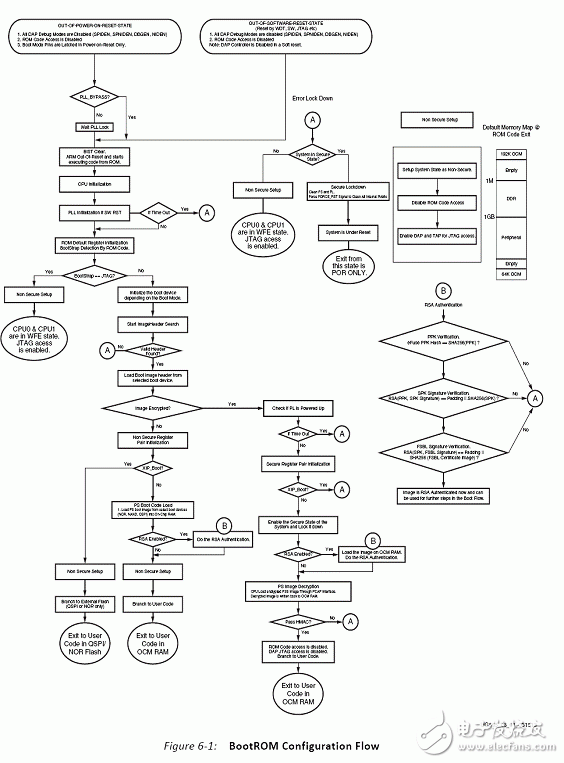
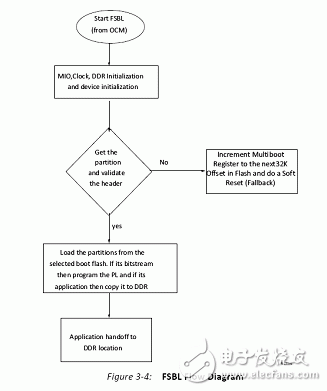
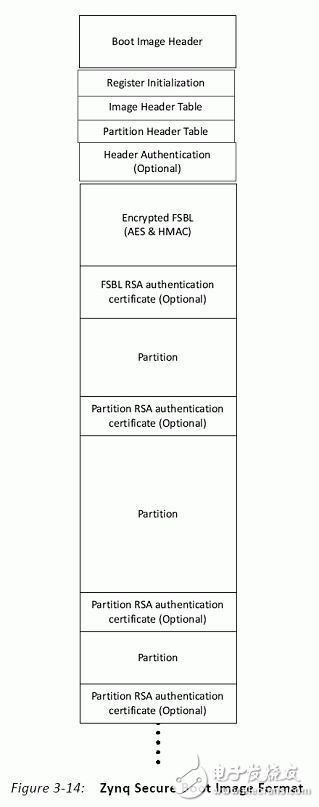
The ZYNQ7000 is vastly different from traditional FPGAs in that it positions itself as an All Programmable Soc (software and hardware programmable system-on-chip), which is considered more accurate as a dual-core ARM A9 processor with FPGA as a peripheral. Its boot process embodies the processor-centric feature. In the past, the FPGA boot process of the processor hard core was to start the logic part and then start the processor. On the contrary, ZYNQ7000 starts the processor and then starts the logic part. The ZYNQ7000 configuration is divided into three phases in sequence: stage0, stage1, and stage2 (optional). Table 1: Configuration steps Table 2: Boot Mode Pin Mapping table 3 figure 1 figure 2 Figure 3 (UG821) ZYNQ7000 provides a number of security modules for customers to call. According to the characteristics of the modules, they can be divided into passive and active. The passive modules mainly include multiple encryption and authentication strategies. The active modules include JTAG shutdown, temperature and voltage monitoring, code consistency detection, and specialization. Sex detection (device DNA), etc., Table 4 details these components, customers can call according to design needs. Table 4: Active and passive protection modules ( 1) RSA user authentication: In some cases, the device has a high requirement for the legality of the source of the program: the program must be activated by a legitimate organization to ensure that the device is operating in a set context, any illegal program or tampering with the legitimate program. The device will not work. The RSA user authentication function provided by the Xilinx Z7 chip is introduced to satisfy the legality of the program. Xilinx uses two sets of public and private keys, one set is fixed and one set is replaceable, thus ensuring higher security. The fixed group is called PPK/PSK (primary public key/primary secret key), and the replacement group is SPK/SSK (secondary public key/secondary secret key). The data to be authenticated is followed by a 1-stage authentication code, which includes: PPK, SPK, PSK, SPK signature obtained after encrypting SPK, SHA-256 digest algorithm to summarize FSBL, and the abstract is encrypted by SSK to obtain signature. This signature is also stored in the authentication code, so the authentication code contains the above 4 pieces of data. The RSA authentication process operates on the information carried by the authentication code. Firstly, the PPK is summarized by the SHA-256 algorithm, and the obtained digest is compared with the value stored in EFUSE. If it is consistent, the process proceeds to the next step; the authenticated PPK team SPK signature is decrypted, and the value after comparison and decryption is consistent with SPK. Go to the next step; SPK decrypts the FSBL signature, and performs SHA-256 digest acquisition on the FSBL. The comparison digest is the same as the SPK decryption value, and the RSA authentication ends. (2), AES encryption and HMAC code authentication: The Xilinx Zynq-7000 protects the customer's intellectual property through the AES-256 decryption engine and the HMAC (Keyed-hashed message authen TIcaTIon code) authentication engine embedded in the chip, preventing copying, copying, etc. from damaging customer intellectual property events. Rationale: Xilinx Zynq-7000 includes AES-256 decryption engine and HMAC authentication engine, and supports Secure Boot boot mode to protect customer's design (including software binary executable code, data and FPGA bitstream programming files) Being stolen and used. After completing the design, the customer can use the Xilinx ISE software to add a 256-bit checksum for authentication to the design, and then encrypt it with the 256-bit key AES algorithm. The 256-bit AES key is generated by the client and stored inside the FPGA and cannot be read externally. At startup, the Zynq-7000 first executes the code in the internal ROM of the chip. The BOOTROM code first decrypts the protected design through the AES-256 decryption engine and then authenticates the integrity through the HMAC engine. Only certified designs can be loaded and executed. For attempts to steal intellectual property through "copy", the content in the FLASH will not be loaded and executed because of the lack of AES keys corresponding to the FLASH content. The combination of 256-bit AES keys reaches 1.15 & TImes; 1077, which can fully guarantee the security of customer intellectual property. Features of the hardware security engine included in the Xilinx Zynq-7000: 1. The HMAC hardware authentication engine protects the customer's design from being tamper-proof in the inner layer to ensure the integrity of the customer's design. Use the SHA256 FIPS PUB-182-2 algorithm and the HMAC FIPS PUB-198 algorithm from the National Institute of Standards and Technology. These algorithms are provided by the National Institute of Standards and Technology (NIST) and signed in Boot Image. in. 2. The AES-256 hardware decryption engine is not reverse engineered in the outer layer protection client design, is not analyzed and cracked, and is not copied. The key is stored on the on-chip eFuse or BBRAM (battery-backed RAM) and cannot be read by JTAG or FPGA logic. eFuse only supports one-time programmable, and the power-down content is not lost. BBRAM supports repeated programming, but the power loss is lost, so an external battery is required. The AES algorithm is the official standard of the National Institute of Standards and Technology and the US Department of Commerce. Xilinx supports the highest security level of 256-bit key encryption and decryption. The 256-bit AES key can be specified by the user, using the Xilinx BitGen tool to generate an encrypted bitstream, or the tool can generate a random key. The AES key is written to the Zynq-7000 chip via JTAG by Xilinx iMPACT software. When writing AES keys, the memory (key memory and configuration memory) in all FPGAs is cleared. After the key is written, there is no way to re-read the written key, and it is impossible to rewrite the key without emptying all the memory. When using BBRAM to save the key, you need to connect the battery to VCCBATT to ensure that the contents of BBRAM will not be lost if the system is powered down. When the system is working properly, the BBRAM is powered by VCCAUX and not powered by the battery on VCCBATT. When the system is powered down, the current required by VCCBATT is small (nA level), and a watch button battery can be used for a long time. In secure boot mode, the PS DAP and PL TAP controllers are turned off, which eliminates the possibility of accessing the internals of the chip through JTAG. The PS's DAP controller can be permanently turned off by eFuse's JTAG CHAIN ​​DISABLE. When generating a PL bitstream, the DISABLE_JTAG option can be configured to disable access to the PL via JTAG. (3), specific detection (DNA, etc.): Each XILINX chip has a unique 57bit serial code corresponding to the chip's DNA. When the specific detection is enabled, the detection circuit compares the CRC check code generated based on the internal serial code with the external flash input. Code, consistent to start the design. Since each chip needs to generate a separate configuration code, it is inconvenient for mass production. In order to solve this contradiction, some chips provide a 32-bit one-time programming efuse, and the user-defined 32-bit serial code is stored. This resolves the above contradiction. The protection strength of the specific detection is limited by the number of serial code bits, and is less than RSA, AES+HMAC authentication. (4), voltage temperature monitoring: ZYNQ7000 built-in temperature and voltage sensor, with on-chip AD, can monitor the temperature and voltage of the chip. Illegal reading or tampering with internal information is often accompanied by abnormal temperature and voltage. When the change value exceeds the set upper limit, we can choose to wipe. Keys saved in addition to internal efuse or BBRAM; (5), JTAG is closed: The most common method of illegal reading or tampering is to peek through the on-chip program through the JTAG port. For this illegal behavior, the XILINX device can close the JTAG port by various means, such as efuse-enabled permanent shutdown, calling the BSCANE2 module in the code. Off, bitgen settings are off. The above means physically cut off the peeping path, and also brings inconvenience of debugging. Once the JTAG port is closed, it must be configured with other configuration devices. (1), key file generation When adding the FSBL file, you must select the aes encryption option, otherwise sdk will report an error. This is because zynq determines whether to call the decryption module by encrypting the FSBL. Therefore, if you want to generate an encrypted image, the FSBL must be encrypted. At the same time, the bitsream file must also be encrypted. Encrypted, while other files are free to choose whether to encrypt; (2), KEY programming to write to BBRAM is very simple, add the key file to the PL device, click on the program, but when you write efuse trouble, after the implementation, report warning: The conditions required to view EFUSE programming are as follows: These are the requirements for programming or reading the eFUSE registers using iMPACT: • iMPACT is running on a PC with Microsoft Windows XP (32-bit) or Windows 7 (32-bit or 64-bit) OS. Note Windows 7 64-bit support is only enabled for Zynq-7000 and 7 series devices. • iMPACT is operating in Boundary Scan mode, and the unconfigured target FPGA device is in the chain in the Boundary Scan window. • You are connected to the Boundary Scan chain through a Platform Cable USB II download cable. • The Boundary Scan chain is operating at a cable speed of 3 MHz for Zynq-7000 and 7 series devices, 6 MHz for Virtex-6 FPGAs, or 1.5 MHz or slower for Spartan-6 FPGAs. To set the cable speed, run the Command Output > Cable Setup and set the TCK Speed/Baud Rate option in the Cable Communication Setup dialog box. • The target FPGA is not currently programmed. No bitstream information has been downloaded into the FPGA. • The VCCAUX and VFS (Virtex-6 and Spartan-6 only) voltages supplied to the FPGA are set to the required levels. Voltages necessary for eFUSE reading and writing are described in the following user guides. For reading eFUSE registers, the VCCAUX voltage supplied to the FPGA must be set to the recommended operating condition. For programming Virtex-6 and Spartan-6 eFUSE registers, the VFS voltage supplied to the FPGA must also be set to its recommended operating condition See the following data sheets for the recommended operating conditions of each power supply. (3), JTAG Debug The existence of JTAG is convenient for debugging, but it leaves a security risk. Here are three ways to disable the JTAG port. In Zynq-7000 AP SoC, the JTAG port is used to load software and the bitstream, load the AES key, control information, and for debug. If not disabled, JTAG ports can be used by an adversary to insert malware, and read configuration Memory and registers. The JTAG ports must be disabled whenever it is not used in a legitimate debug operation. The device can be debugged using a DAP controller and/or a JTAG controller. The DAP JTAG chain and PL JTAG chain can be concatenated or used independently. When used independently, the full SoC/FPGA does not need to be exposed to an adversary. For example, if debug only requires access to the PL, the user can select that only PL JTAG chain is used. This prevents access to the PS. Zynq provides hierarchical control of the JTAG port. This allows different methods to control access to the debug ports based on security requirements. Security requirements may change over the life cycle the embedded device. There are three methods to disable the JTAG debug ports. Fielding an embedded device with Zynq, a one-time programmable eFUSE bit can permanently disable access to the debug ports. Programming this eFUSE bit is irreversible, and debug ports remain disabled after powering down and recycling power. The second method, which can be used only if the debug port disable eFUSE is not blown,disables/enables debug access port using the JTAG_CHAIN_DISABLE, DAP_EN, SPINDEN, SPIDEN, NIDEN, DBGEN bits in the Control register at 0xF 8 007000 (see Table 4). The debug access control is provided independently for the two JTAG chains or the concatenated chain. In the third method, a lock register provides semi-permanent disabling of access to the debug ports. In this method, the debug port access disable remains in effect until a power cycle. In a secure boot, the JTAG port is disabled early by the BootROM code. Users who will not use the debug port after product release can disable the JTAG port permanently by writing the eFUSE Disable JTAG register. The disable is done using iMPACT or the Secure Key Driver. Any attempted read or write access to the BBRAM via JTAG causes the BBRAM contents to be cleared and the entire configuration of the FPGA to be erased prior to access being enabled (ie, being able to enter "key access mode"). (4), the highest level of encryption strategy RSA check and AES encryption combined use, currently we only choose AES encryption. On the other hand, it should be noted that since the ZYNQ product even burns the KEY file, if the image startup file is non-encrypted, the device can still be started. For professionals who understand this feature, they can load a non-encrypted file. Start the device, then open the key's read interface in your own code, steal the key file, and then crack the encrypted file. Therefore, in order to prevent such stealing events, we can only start from efuse encryption (another way is to use RSA to verify the startup file). Summarize our encryption strategy, EFUSE save, JTAG shutdown, start only from efuse encryption. We can follow customers' drawings or design to make Customized wire
harness for various industries: game machine, ATM, POS machine, etc.
Customized
wire assembly with AVL components from original manufactures. Also
harness with local equivalent componets are workable with short L/T and
competitive price, also flexible MOQ.
Medical Wire Assemblies,Medical Alligator Clip Cable,Medical Cable Assembly,Medical Wire Harness,Medical Cable ETOP WIREHARNESS LIMITED , https://www.etopwireharness.com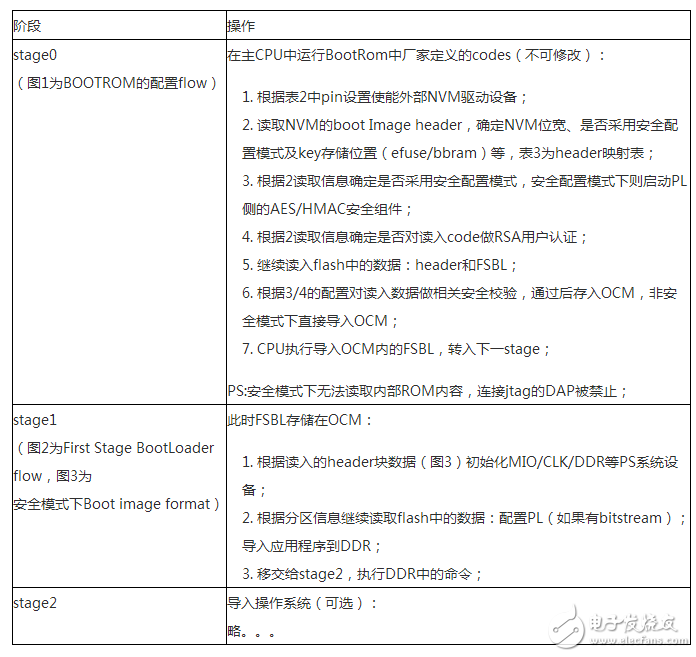
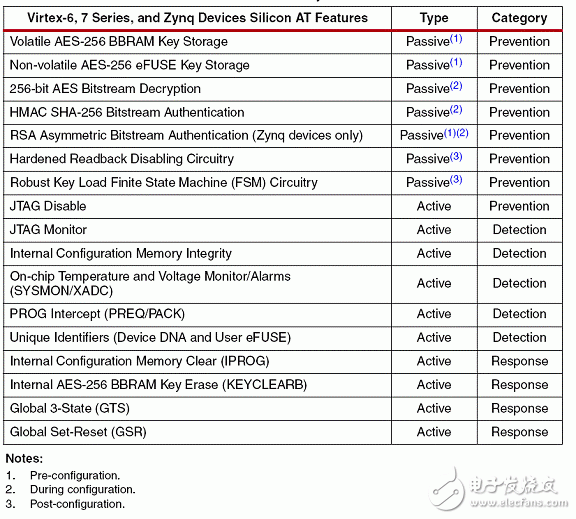
The active and passive modules cooperate with each other to complete the safety design of the project. The following sections describe the common security policies.
RSA is an asymmetric encryption technology that, when used in conjunction with digital signature technology, can authenticate the legitimacy of related data. 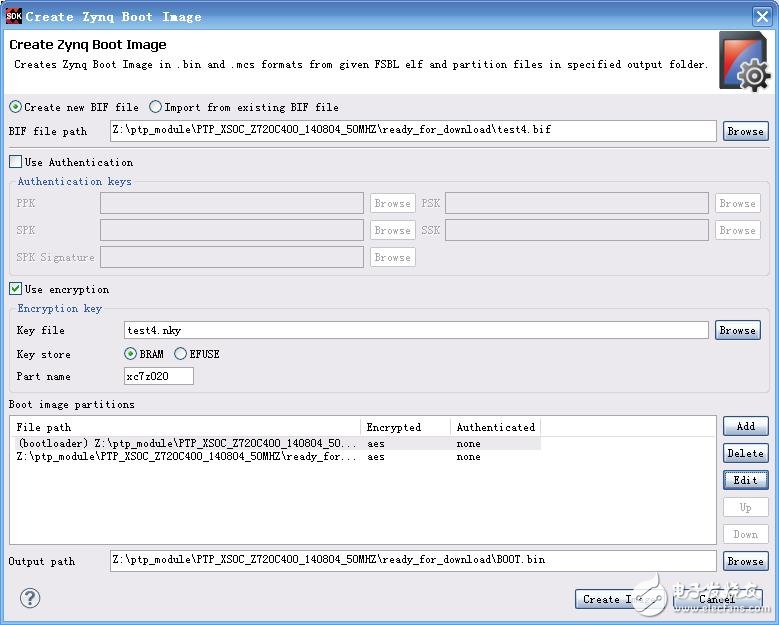
The above picture is the content required to generate image using sdk14.1. If the key file needs to be generated, fill in the file name of the key file in the key file line, select the storage medium in the key store, and fill in the device name selected in the project. Xc7z020, if you fill in the error here will affect the impact programming.
The key to AES encryption is the protection of the key. ZYNQ provides two kinds of security methods. BBRAM and eFUSE, BBRAM is more secure, but the maintenance is slightly complicated. The efuse fuse storage method may be physically cracked, but this also requires a considerable technical background. And special equipment is available. Therefore, considering various factors, choose EFUSE mode to save the AES key file.
At the same time, because the JTAG port has certain security risks, it may be called by the person who is proficient in the device and related background knowledge to read the KEY file, so the JTAG port is permanently closed after the product is finalized.