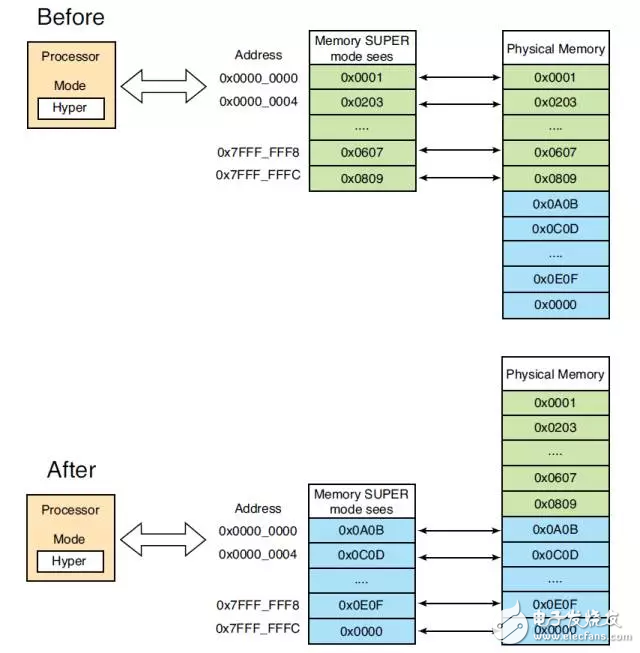
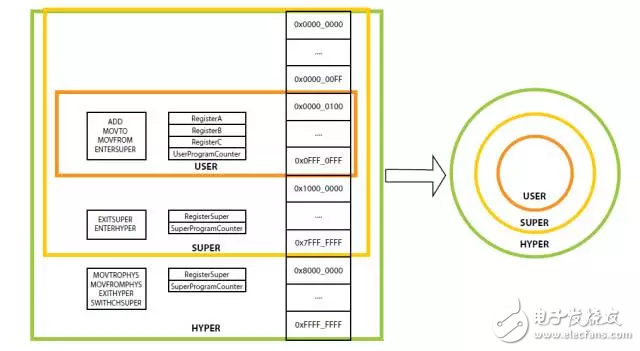
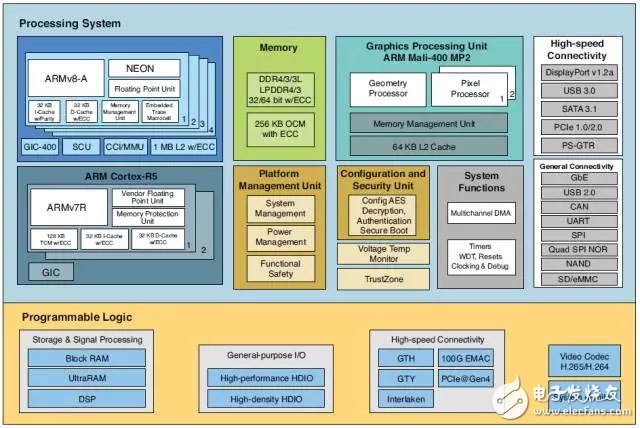
Get familiar with the Xen hypervisor running on the Xilinx Zynq UltraScale+ MPSoC with this fun tutorial. When Xilinx and DornerWorks' system software team launched the Xen Project hypervisor on Xilinx's Zynq® Ultrascale+TM MPSoC, we found that we could demonstrate and test the system by running the popular video game Doom. What? ! You don't know DOOM? ? (CS you always know -__-||) How to run Doom on Xen with QEMU for Zynq UltraScale+ MPSoC Before we go into the details, let's take a look at what the hypervisors are and how they work with the processors on the Zynq UltraScale+ MPSoC. Management program and how it works A hypervisor is a computer program that virtualizes a processor. Applications and operating systems running on virtualized processors appear to have full ownership of the system, but in fact the hypervisor is responsible for managing virtual processor access to physical machine resources such as memory and processing cores. Managers are popular because of the isolation between design partitions and independent software elements running on the system. To support virtualization, the physical processor must provide a special "mode" for the hypervisor to run. Therefore, introducing the processor pattern helps to understand how the hypervisor completes processor magic. All processors have instructions that manipulate the values ​​stored in the registers and can read and write to the memory. The processor's mode is a collection of instructions and registers, as well as the rules to follow when accessing registers and memory with instructions. For ease of explanation, we use a general-purpose processor as an example and use terminology that is not related to structure. In this example, the processor has specific registers, instructions, and modes. The registers include RegisterA, RegisterB, RegisterC, UserProgramCounter, Register-Super, and SuperProgramCounter. The instructions include the following. ADD Register3 Register1 Register2 Adds Register1 and Register2 and stores the result in Register3, Register3 = Register1 + Register2. MOVTO Register2 Register1 Moves the memory contents pointed to by the address in Register1 to Register2. MOVFROM Register2 Register1 Moves the contents of Register1 to the memory pointed to by the address in Register2. ENTERSUPER enters the processor's SUPER mode. EXITSUPER exits SUPER mode and enters USER mode. In USER mode, the functionality of the processor's instructions is limited. In this example, the instruction can read and write to all registers except RegisterSuper and SuperProgramCounter, and the processor can execute all instructions except EXITSUPER. In addition, in USER mode, all instructions can only read and write a portion of the memory, for example from address 0x0000_0100 to 0x0FFF_FFFF. In USER mode, if the program attempts to execute an instruction that should not be executed, or accesses a register or memory location that is not authorized to access, the processor will suspend the error instruction (offending instrucTIon). In SUPER mode, the processor's instructions can read/write all of the above registers, including RegisterSuper and SuperProgramCounter. All the commands listed above, including EXITSUPER, can be executed. In addition, the additional command ENTERHYPER is also executable (more on this later). In addition, in SUPER mode, instructions can access all of the memory in the system (from 0x0000_0000 to 0x7FFF_ FFFF). With a processor with a pattern, we can use design partitions to solve software engineering problems more easily. In the above example, there is only one way to enter the SUPER mode: execute the ENTERSUPER instruction. Again, there is only one way to exit SUPER mode: execute EXITSUPER. In addition, the program can only access part of the machine's memory in USER mode. With this approach, we can write a program that lets the processor run multiple USER mode programs at the same time. This "OS" program runs in SUPER mode and manages programs running in USER mode. When the OS is running, it will look at all the USER mode programs that need to be run, select a run, and then use an instruction such as EXITSUPER to tell the processor to switch to USER mode to run the program. The selected program will run until an event causes the processor to switch back to SUPER mode. This type of event can be an ENTERSUPER instruction from the USER mode program, or an external event, such as a timer, which does not alert the program that is running in USER mode to switch the processor to SUPER mode. Regardless of how the switchover occurs, whenever an event occurs, we can build an OS to select and run programs one after the other based on the appropriate policy. When the switch is fast, the user thinks the USER program is running at the same time. The use of USER HYPER mode is to have many SUPER programs run. Each program in SUPER mode can be an OS; these OSs themselves will allow many USER programs to run in parallel. The SUPER processor mode also prevents the USER program from interfering with programs running in SUPER mode or other USER mode programs. Any errors or violations of the USER mode program can be controlled in the program's own instance without disrupting or interfering with system memory and registers reserved for SUPER mode operations. Sounds great, but can you implement some functions in another mode? With a little extension to our machine, you can introduce HYPER mode. HYPER mode can read/write all initial registers (RegisterA, RegisterB, RegisterC, UserProgramCounter, RegisterSuper, and SuperProgramCounter) and two additional registers: RegisterHyper and HyperProgramCounter. The instructions in HYPER mode include the initial set and the italics below. ADD Register3 Register1 Register2 Adds Register1 and Register2 and places the result in Register3, Register3 = Register1 + Register2. MOVTO Register2 Register1 Moves the memory contents pointed to by the address in Register1 to Register2. MOVFROM Register2 Register1 Moves the contents of Register1 to the memory pointed to by the address in Register2. MOVTOPHYS Register2 Register1 Moves the memory contents pointed to by the physical address in Register1 to Register2. MOVFROMPHYS Register2 Register1 Moves the contents of Register1 to the physical memory pointed to by the address in Register2. ENTERSUPER enters the processor's SUPER mode. EXITSUPER exits SUPER mode and enters USER mode. ENTERHYPER enters the processor's HYPER mode. EXITHYPER exits the processor's HYPER mode. SWITCHSUPER RegisterHyper switches to the SUPER program, which will use the value in RegisterHyper to execute the next SUPER program. Additional instructions and registers in HYPER mode allow the processor to switch which program to run in SUPER mode, just as SUPER mode allows the processor to switch which program to run in USER mode. One of the features of HYPER mode is the ability to switch which memory SUPER mode can be seen; when a program running in HYPER mode executes SWITCHSUPER RegisterHyper, the underlying memory is completely broken. This means that when the program in HYPER mode executes EXITHYPER, the actual physical memory seen by SUPER mode is different from the physical memory used by another program running in SUPER mode when the next SUPER program runs. The SUPER mode program still uses the same address to access the memory, but the address points to a different physical location. Figure 1 shows the processor memory view before and after executing SWITCHSUPER RegisterHyper. The HYPER mode is useful because it allows many SUPER programs to run. Each program in the SUPER mode can be an OS; these OSs themselves allow many USER programs to run side by side. This means that we can run multiple OSs on the same hardware, such as Windows and Linux; run 20 on one processor Linux instance; or any combination between them. Since each virtual OS instance cannot see another OS instance, if one crashes, it will not crash another instance. There are other applications for HYPER mode: we can partition system resources between multiple OSs; monitor the execution of each OS in HYPER mode to restart on a crash; and keep a close eye on system state while the virtual OS is running. Figure 1: Differences before and after executing SWITCHSUPER RegisterHyper in HYPER mode As the processor switches from USER to SUPER mode and then switches from SUPER to HYPER mode, the machine gives the execution code more privileges. In this example, the USER mode program only has four registers (RegisterA, RegisterB, RegisterC, and UserProgramCounter) and four instructions: (ADD, MOVTO, MOVFROM, and ENTER-SUPER). In addition, the USER program can only read and write memory from 0x0000_0100 to 0x0FFF_FFFF. Once in SUPER mode, the processor allows instructions to talk to RegisterSuper and SuperProgramCounter and allows EXITSUPER and ENTERHYPER to be executed. In addition, the SUPER program can access memory from 0x0000_0000 to 0x7FFF_FFFF. Finally, once the processor enters HYPER mode, its instructions can operate RegisterHyper and HyperProgramCounter, and the program can execute SWITCH-SUPER and EXITHYPER. Figure 2: Various modes as shown in the ring HYPER mode also allows the processor to read and write all virtual memory, 0x0000_0000 to 0xFFFF_FFFF, and read and write actual physical memory. These privilege levels are usually visually described in a ring (Figure 2). The primary ring, the HYPER ring, grants privileges to rings with lower privilege levels and ultimately controls the entire system. Theory and practice ARM® creates processor designs for ARM partners to build chips. An ARM processor contains one or more cores. Each core implements an ARM architecture. For example, the Zynq UltraScale+ MPSoC includes an ARM CortexTM-A53 processor and four ARMv8-A physical cores (Figure 3). This distinction is important when looking at the documentation and code of an ARM processor; for a complete understanding of the "chip" with an ARM core, refer to the documentation for architectures such as ARMv8-A and processors such as Cortex-A53. . There are four exception levels in the ARMv8 architecture (Source: ARM Architecture Reference Manual, D1-1404): 1. Exception level 0 (EL0), can be executed without privilege; 2. Exception level 1 (EL1), the execution of the OS and the contents of any privileged instructions; 3. Exception level 2 (EL2), allowing hardware to be virtualized; 4. Exception Level 3 (EL3) allows switching between safe and non-secure processor states. The following programs typically run in these modes, as described in the ARM Architecture Reference Manual (D1–1404): EL0, Application; EL1, OS Kernel, and the associated privileged functions commonly described; EL2, Hypervisor; EL3, Security Monitoring Device. Our theoretical example directly corresponds to ARMv8 execution mode EL0 to EL2: USER corresponds to EL0, SUPER corresponds to EL1, and HYPER corresponds to EL2. ARM adds a fourth privilege level, EL3; with this privilege level, we can switch between EL0 and EL1 between secure and non-secure environments. Although the use of EL3 is an important topic that can add a lot of functionality to the architecture, we ignore it in this example and focus on EL0-EL2 (using hypervisor virtualization). If you are interested in how your computer protects financial transactions, you can refer to the ARMv8 EL3 documentation (available for free, registration required). This is a very good reference document from which you can get a very detailed introduction. Figure 3: Zynq UltraScale+ MPSoC Architecture Digital Signage For Bank,Signage Screen,Digital Signage Advertising,Smart Digital Signage Guangdong Elieken Electronic Technology Co.,Ltd. , https://www.elieken.com