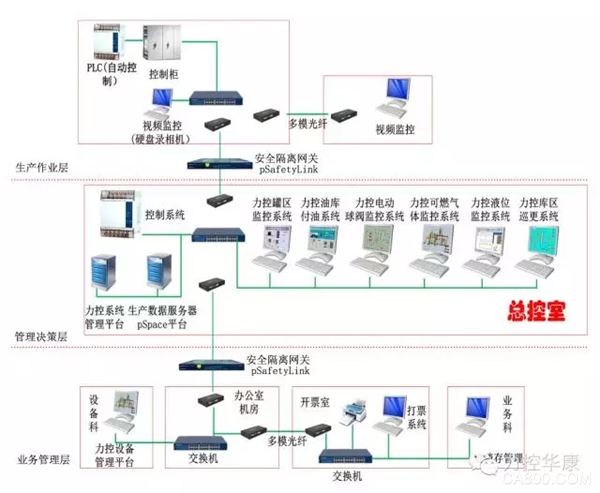
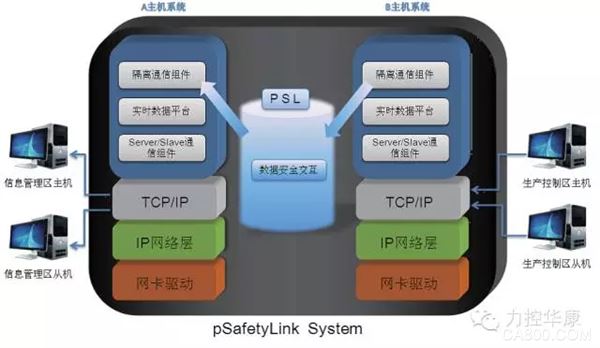
1. Project Overview China Petroleum Tibet Sales Branch 725 oil depot is located in the western suburbs of Lhasa City, Tibet Autonomous Region. The oil depot was built in May 1972. The total oil storage capacity of the oil depot reaches 86,000 m3, which is a secondary oil depot. The original 25 oil tanks in the oil depot have a total capacity of 86,000 tons. The oil depot operates five kinds of oil products. The main oil products are all imported from the troop pipelines. Other oil products are transported by motor vehicles. The oil delivery system has 3 platforms and 12 cranes self-discharged oil delivery facilities, and imports and exports 240,000 tons of oil products annually. The 725 oil storage project in Tibet will be based on a refined oil depot management system and will be integrated with management and decision-making, business management, and production operations. The integration of production, supply and sales will enable all production data to be accessed in real time. In order to prevent viruses and hackers from entering the production network of the oil depot, and thus affecting the safety of the entire oil storage, in this case, we must pay attention to the safety of data transmission and do a good job of ensuring the boundary safety of industrial control systems. In this project, the data of the production layer of the 725 oil storage in Tibet was safely transmitted to the management of the 725 oil storage in Tibet through force-controlling the pSafetyLink of the Huakang Industrial Separation Gateway, effectively preventing hackers and viruses from attacking the control network. 2. Solution The system structure of the 725 oil depot project in Tibet can be divided into three levels: management decision-making level, business management level and production operation level according to business functions. The main management and decision-making layer of the business management shall extract production data related to the oil depots for use in production scheduling and command, complete various controls, monitor operating parameters, report alarms and trends, and manage oil business operations such as import, sales, and storage. Each security loophole in an industrial control system can lead to unpredictable and severe consequences. Therefore, it is necessary to physically isolate the business management layer, management decision layer, and production operation layer. The system of the 725 oil storage project in Tibet divides the structure of the enterprise information system into different regions, and establishes an effective "depth defense" system for information security of the control system. In the oil depot production operation layer and the oil tank management level, the management and the business management level use force to control the pSafetyLink of Huakang Industrial Safety Isolation Gateway, and pSafetyLink realizes effective boundary isolation between the oil depot production operation layer, business management layer and management decision-making layer. Under the premise of ensuring the effective data communication between the oil depot production operation layer, business management layer and management decision-making layer, effectively protect the production network from viruses and hackers, which is the production layer, business management layer and management decision layer of the oil depot. Connections provide security. The security isolation gateway has a special 2+1 dual independent host architecture. The control end accesses the industrial control network, collects the data of each subsystem through the acquisition interface, and accesses the enterprise management network to complete the data transmission to the dispatch center. Between the two hosts through a proprietary PSL network isolation transmission technology, truncate the TCP connection and completely cut through the penetrating TCP connection. The physical layer of the PSL adopts dedicated isolation hardware. The link layer and application layer adopt a private communication protocol, and the data stream is transmitted in a 128-bit or more encrypted manner, which fully ensures data security. PSL technology realizes data self-definition, self-analysis, and self-censorship. The transmission mechanism is completely inoffensive, and fundamentally eliminates the passage of illegal data to ensure that the subsystem control system will not be attacked, invaded, and infected by viruses. Product Features 1. "2+1" isolation technology architecture Ensure the normal communication between networks, and completely block the direct TCP/IP connection between networks and cut off the carrier of attacks. 2. One-way data transmission When production data is uploaded to the information network, various threats are blocked from being transmitted to the control network. 3. Dual data ferry mode Measuring point control mode: According to the needs of industrial field data communication, it provides analysis and security protection of measurement point data; Tunnel control mode: Use self-developed secure data transmission methods to support data transfer in more diverse network environments such as general IT traffic, video traffic, and relational database traffic. 4. Multi-protocol data aggregation distribution Supports common industrial protocols such as OPC, Modbus, IEC60870-5-101/102/103/104, and various PLC Ethernet communications to support data multiplexing to different upper systems. 5. Broken Cache Data integrity, continuity and reliability are ensured, and data is recorded automatically when the communication link is disconnected. 6. Hot standby The failure of the equipment itself will not affect the normal business flow at the site, so as to improve the stability of the system and ensure the continuity of the business. 7. OPC tunnel Simplified DCOM configuration procedures, improved work efficiency, and greatly reduced maintenance costs. User value 2 Thoroughly isolate the spread of malicious programs such as worms and Trojans in IT networks - protect the safety of important assets such as SCADA, DCS, and PLC. 2 Filter out malicious code embedded in the application layer - protect the safety of factory production equipment. 2 Thoroughly block malicious attacks such as ARP, flood, fragmentation, and malicious scanning - protect plant production equipment from malicious attacks, thereby protecting plant life and property safety. 2 Industrial-grade reliability, long-term stable operation of equipment - Ã improve system stability and ensure business continuity. 3, protective effect pSafetyLink has been put into operation since December 2009 and has operated steadily so far. pSafetyLink provided a powerful guarantee for the network data security of the control system of the 725 oil storage project in Tibet.
Our banknote handling machines mainly include following
BC -30: basic piece counter with only one UV
BC-35: piece counter with UV MG
BC-40: value counter with one CIS, support 4 currencies, Auto recognition, multi-currency mix counting
BC-55: value counter with two CIS, support 40 currencies at the same time, serial number reading, Auto recognition, multi-currency mix counting, remote software upgrading via network
Those 4 models have similar structure, passage can be opened from reat side, easy for maintenance and cleaning
BCS-160: 1+1 Pockets Banknote Sorter with two CIS, support 20 currencies at most, serial number reading
Banknote Deposit Machine,Mixed Denomination Cis Banknote Counter,High Speed Euro Banknote Counter,Mixed Denomination Cis Banknote Counter Suzhou Ribao Technology Co. Ltd. , https://www.ribaoeurope.com