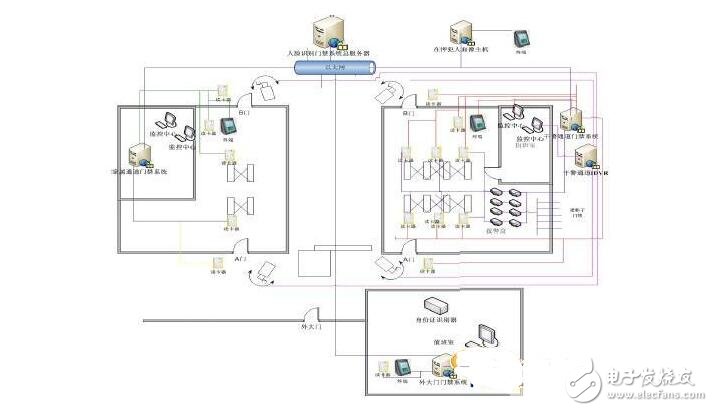
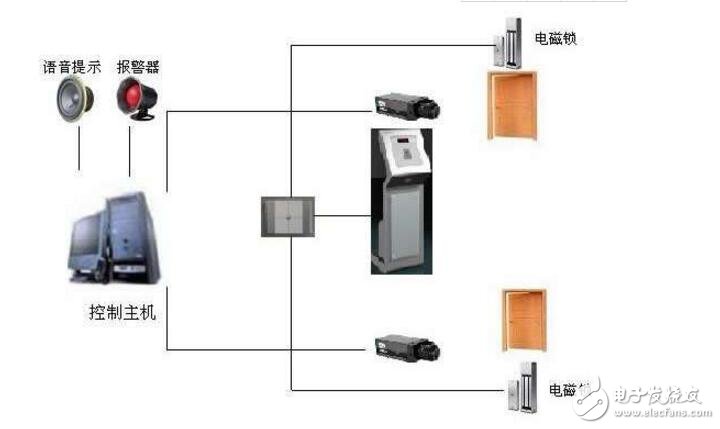
Abstract: At present, the face recognition access control system is more and more widely used in our life. This paper analyzes the key points of the face recognition access control system in detail and introduces the prison face recognition access control system scheme and the prison face recognition access control system in detail. Program. To design an access control system, the first thing to consider is system security, that is, whether it can effectively control the access of personnel and master the information of its access. Because the IC card access control system is an intelligent electronic control system, it can make full use of the "smart" of the computer, and at the same time use a variety of means to control to ensure the system is safe and reliable. The simplest and most effective of these are the following. First, the password is set by the password set in the IC encryption card. If the password is not correct after several times (usually three times), the card will be automatically burned and cannot be used. This can effectively prevent malicious verification of theft of user information. The second is to use the user permission table in the system to re-authenticate whether the cardholder can enter the door. The third is to set an effective use period on each IC card. If the IC card exceeds the validity period, all the data of the user will be automatically deleted from the access control subsystem control module, and the card is invalid. Can be considered from two aspects of software and hardware. Face recognition access control system scheme, hardware reliability, in addition to electrical control locks and other mechanical components, mainly consider the production and selection of sub-control modules, because it must work 24 hours a day, so its performance requirements are more High, should be able to meet the changes in the temperature and humidity of the environment, as well as strong anti-electromagnetic interference. If the Newton 7000 series module is selected as the sub-control module, because this module has a strong adaptive function, it can automatically adjust the signals of different baud rates, as well as various protection circuits, etc., which can ensure the needs of low-level management work. . The reliability of software design mainly considers the acquisition and maintenance of various state information, whether the design of the communication protocol is standardized, whether the processing of various special cases is reasonable, and so on. For example, in order to ensure accurate communication between the host computer and the sub-control module, an automatic retransmission error correction mechanism can be adopted to effectively eliminate signal conflicts that may occur when the access control subsystem and the management computer are working in the network at the same time. Since the setting and management of all data information in the system is completed by communication between the host computer and the sub-control module. Managers can freely set passwords, user rights, door lock delays, etc. according to their needs. At the same time, the main control computer and the sub-control module work independently at the same time. Only when the initial data in the sub-control module is set, the data in the sub-control module is modified, and the information recorded in the sub-control module is acquired, the two need to communicate with each other. , exchange information. This design approach gives the system a lot of flexibility. In order to reduce the hardware cost, a sub-control module can be designed to control multiple gates at the same time. For example, when using the I-7188 as a sub-control module, one sub-control module can control three gates at the same time. In fact, this configuration is equivalent to one. A macro parallel processing mechanism. The user permission table can be arbitrarily set by the administrator, and it is very flexible to use. It is easy to meet different requirements such as "one door one card", "one door multi card" and "multiple door one card". The face recognition access control system scheme, the user's needs are constantly changing, there should be some room for designing the system to ensure the dynamic needs of users. For example, each sub-control module in the system has a unique address. When it is necessary to increase the number of controlled gates, just add a corresponding number of sub-control modules and access control subsystems, and assign a unique address to the sub-control modules. If the Newton 7000 series industrial control module is used as the sub-control module, 256 modules can be connected to one RS485 network. With the advancement of prisons, the traditional monitoring and management model faces the challenge of reform. On the one hand, the form of security and security is becoming more and more serious; on the other hand, institutional compression and personnel streamlining. The new situation has created new demands for security work. Under the unified arrangement of the prison, the face recognition access control system was set up in the area according to the technical requirements, and the system was rationally and effectively integrated to achieve the organic combination of physical defense, technical defense and civil air defense. The prison gate and the AB gate are important parts of the supervision site and the outside world. In order to strictly control the monitoring area, the production area personnel access, prevent criminals from escaping, achieve effective unified command, ensure the safety of the supervision place, install intelligent face recognition management system at the prison gate and AB door. The prison face recognition access control system consists of the following six subsystems: 1) Access control system outside the prison gate 2) Dry police access control system 3) Meeting with the family access control system 4) Vehicle access control system (shared with a system of police channels) 5) Attendance system 6) Custody face management system 1) Access control system outside the prison: the ID card identification system is used in conjunction with the face recognition system to strictly control the entry and exit of outsiders and avoid the possibility of criminals using the alien to escape from prison; this system is used for data of all police officers in the prison. Entry, including face-to-face collection, personal information software, party cards, and registration of outsiders, including ID card identification, face-to-face collection, personal information input, and temporary cards. 2) Traffic police access control system: IC card plus infrared face recognition, dual verification, face IC card technology based on the uniqueness, certainty and classability of the face, advanced face recognition technology and smart card reading and writing The technology is highly integrated, with all the functions of surface acquisition and IC card reading and writing, and high efficiency, accuracy and security. It can strictly supervise and control the entry and exit of each police officer and outsiders, and prevent the entry and exit of non-permitted personnel. In addition, the alarm box matrix is ​​formed with the access control system, and is used for the police officers to automatically pop up the corresponding cabinet when the A card is used to exchange the B card. 3) Meet the family access control system: the combination of face recognition + IC card to ensure the high degree of uniformity of the entry and exit personnel, to prevent the prisoners from moving away from this channel, and strictly control the personnel's outing. And perfect use with the butterfly gate. 4) Vehicle access control system (shared with the police channel): It is used in conjunction with the police access control system and strictly controls the entry and exit of foreign personnel. 5) Attendance system: Infrared face recognition access control system has both attendance system. At the same time, according to the actual situation of each door, only IC card attendance system can be used. Face recognition and IC card management can be combined arbitrarily for convenient management. 6) Detainee face management system: Using infrared face recognition technology, all the criminals in custody are entered into the system database to strictly manage the criminal's personal data. This system is installed in the Investigation Section and manages personnel data for all detained criminals. 4.1 System Description and Configuration Introduction 1) Install a set of face recognition access control management system host at the gate outside the prison, externally connect a face recognition terminal and a card reader (using dual camera terminals, color + infrared), and install a set of ID card identification system. 2).1 set of face recognition access control management system host, external 1 face recognition terminal and 9 card readers (using dual camera terminal, color + infrared); install a set of face recognition IDVR, connect the police channel and family channel Camera outside the AB door (IDVR function: in addition to the DVR function, there is another face capture function); install 8 alarm box matrix, connect with the access control system, and connect the cabinet lock of 1000 cabinets, which is convenient for automatically popping the cabinet Change the B card. 3) 1 set of face recognition access control management system host, external 1 face recognition terminal and 5 card readers (using dual camera terminal, color + infrared); 4) Install a set of face recognition in the investigation department (or other departments) in the prison face management system host, and connect a face recognition terminal (using a dual camera terminal, color + infrared) 5) Install face recognition server in the general monitoring room for backup data, data and attendance system, human resource management, attendance; database establishment, all face recognition access control subsystem and the prison management system shared server Database, easy to manage, and share information in a timely manner. 6) Install the emergency door open button on the inside of the A door, the outside of the B door, and the duty room or the general monitoring room. Install the door open button on the inside of the A-door and the outside of the B-door outside the office desk or in the monitoring room to facilitate the urgent need to activate the button to open the door. ) In addition, due to emergencies, for example, in the case of an emergency in the prison area, a large number of police forces are required to enter the prison area, and the butterfly gate can be normally opened or normally closed. This feature can be implemented in 2 ways: A. As mentioned above, in the duty room setting button, a button with password control can be installed as needed to prevent others from entering the duty room to maliciously control the button. B. Use the software management control function, set the management authority, and realize the normally open or normally closed of the butterfly gate. This option is recommended. First of all, all police officers must go to the gate registration office outside the prison, use the face recognition access control management system to register personal information, issue a new A card, and automatically generate a corresponding B card. The A card is worn by the police outside the supervision area, and the B card is stored in The cabinet of the police passage is used for wearing in the supervision area. And enter 5 infrared images of the person as a template and a color image to be archived and verified and authorized. When the police enters the surveillance area, go to the door of the police channel A and place the IC card on the card reader. After confirming, the camera of the IDVR system at the A gate performs real-time recording and immediately captures the image of the police face, and pops up in the duty room in real time. On the monitoring LCD screen, the on-duty personnel compare this captured photo with the personal information on the IC card. After the determination, the A-door is opened by the duty answerer to allow the person to enter. Police officers must look at the camera above the door consciously and cooperatively to capture the face. After entering the A door, the police officer uses the A card to swipe the card reader on the butterfly pad, and displays the personal information on the monitor of the duty room. The access control system sends an instruction to the alarm box, and the alarm box immediately issues an instruction to the corresponding storage card cabinet. The corresponding storage card cabinet is automatically popped up. After the manual personnel perform manual comparison, the A card is exchanged for the B card, and the on-duty personnel open the B door to let the police enter the supervision area. 4.2 Introduction to System Process 4.2.1 Police channel Police ---enter First of all, all police officers must go to the gate registration office outside the prison, use the face recognition access control management system to register personal information, issue a new A card, and automatically generate a corresponding B card. The A card is worn by the police outside the supervision area, and the B card is stored in The cabinet of the police passage is used for wearing in the supervision area. And enter 5 infrared images of the person as a template and a color image to be archived and verified and authorized. When the police enters the surveillance area, go to the door of the police channel A and place the IC card on the card reader. After confirming, the camera of the IDVR system at the A gate performs real-time recording and immediately captures the image of the police face, and pops up in the duty room in real time. On the monitoring LCD screen, the on-duty personnel compare this captured photo with the personal information on the IC card. After the determination, the A-door is opened by the duty answerer to allow the person to enter. Police officers must look at the camera above the door consciously and cooperatively to capture the face. After entering the A door, the police officer uses the A card to swipe the card reader on the butterfly pad, and displays the personal information on the monitor of the duty room. The access control system sends an instruction to the alarm box, and the alarm box immediately issues an instruction to the corresponding storage card cabinet. The corresponding storage card cabinet is automatically popped up. After the manual personnel perform manual comparison, the A card is exchanged for the B card, and the on-duty personnel open the B door to let the police enter the supervision area. ---Out of the supervision area The policeman takes the B card to the door of the police channel B and puts the IC card on the card reader. After confirming, the camera of the IDVR system of the B door performs real-time recording and immediately captures the image of the police face, and pops up in the duty room to monitor the liquid crystal display in real time. On the screen, the duty officer compares the captured photos with the personal information on the IC card. After the determination, the duty answerer opens the B door and allows the person to enter. Police officers must look at the camera above the door consciously and cooperatively to capture the face. After entering the B-door, the police must go to the front of the face recognition terminal, swipe the card, and perform face recognition. The terminal will quickly recognize and capture a color photo archive for easy inquiry. After the verification is successful, the LCD screen below the terminal will display the card number, time and other personal information of the police, the access control system and quickly pass the alarm box, automatically open the corresponding storage card cabinet, and promptly indicate the position of the dry police card cabinet, on duty The person takes out the A card, puts the B card into the storage card cabinet, and sends the A card to the police officer. The police can leave the A door. If the face recognition verification is unsuccessful, the system quickly identifies the captured face image with all the criminals in the database. When the person is found to be a criminal or other undocumented person, the system automatically issues different levels of alarms. foreign workers ---enter When an outsider enters the supervision area, he must first use the identity card of the person to verify the ID card identification system outside the prison gate. When verifying that the ID card is a valid ID card, the access control system is used again, and the duty officer is assigned a new card to the outside. Personnel, and enter personal information and collect 5 infrared image templates and 1 color, and verify. The outsiders are led by the police officers and enter the supervision area by the police channel. The police officers enter the process as above, and the outsiders only need to follow the police. ---Out of the supervision area Outsiders and police officers came to the B-gate. Two people were required to put the IC card on the card reader. After confirming, the camera of the IDVR system of the B-door system recorded the video in real time and immediately captured the image of the police face, and popped up on duty in real time. On the LCD monitor screen, the on-duty personnel compare this captured photo with the personal information on the IC card. After the on-duty personnel have confirmed both of them, the duty answerer opens the B door and allows access. After entering the B-door, both the police and the outsiders must go to the front of the face recognition terminal, swipe the card, and perform face recognition. The terminal will quickly recognize and capture a color photo archive for easy access. After the verification is successful, the LCD screen below the terminal will display the card number, time and other personal information of the police officer and the outside personnel. The access control system quickly passes through the alarm box, automatically opens the corresponding memory card cabinet, and promptly displays the dry police card cabinet. Position, the duty officer takes out the A card, puts the B card into the storage card cabinet, the A card is sent to the police officer, and the police and outside personnel can leave the A door. If the face recognition verification is unsuccessful, the system quickly identifies the captured face image with all the criminals in the database. When the person is found to be a criminal or other undocumented person, the system automatically issues different levels of alarms. 4.2.2 Meeting with family members ---enter When the family enters the supervision area, the identity card identification system must be used to verify the ID card. ) For family members, enter personal information and collect 5 infrared image templates and 1 color, and verify. The family members enter the supervision area by meeting the family channel, go to the door of the family channel A, and put the IC card on the card reader. After confirming, the camera of the IDVR system of the A doorway performs real-time video recording and immediately captures the family face image, and pops up in real time. The duty room monitors the LCD screen, and the on-duty personnel compares the captured photos with the personal information on the IC card. After the determination, the A-door is opened by the duty answerer to allow the person to enter. After entering the A-door, the family members use the temporary card reader to swipe the card on the butterfly gate, and display the personal information on the monitor of the duty room. After the manual personnel perform the manual comparison, the B-door is released, and the family member must be after the A-door brush. It is only effective to swipe the card on the butterfly gate. ---Out of the supervision area When the family members leave the supervision area from the family passage, the process is the same as that of the foreign personnel from the police channel. 4.2.3 Vehicle entry The vehicle is inspected by the existing system of the prison. If the vehicle is a police officer or an outsider, the above procedures are required to enter the surveillance area. 4.3 Single access control system 4.3.1 Access Control Management System Host The access control system host is a highly intelligent computer that works independently and is managed by the management and monitoring computer. The access control system host has the following functions: a) Face recognition: The face information collected by the face collector is compared and identified to confirm the legitimacy of the user. If it is a legitimate user, it will send a door open signal to the electric door, and control the door. If it is an illegal user, it will refuse to open the door. b) Data storage: store all setting parameters, face information, and door opening records of the subsystem. c) Lock control: The access control signal (such as the door status signal) input through the lock controller is processed to control the lock controller. d) Execute the command of the management monitoring machine: accept the command of the management monitoring computer, output the access control signal (open the door, close the door, the door is normally open for a certain period of time, the door is normally closed for a certain period of time) and the alarm signal is given to the lock controller. , to achieve remote control functions. e) Signal acquisition: output the lock status signal collected by the lock controller to the monitoring computer to centrally monitor the working status of each subsystem; f) Open door record output: output the door open record to the management monitoring computer. In the monitoring center, the entry and exit status of each access control point person can be queried in real time, and the access control report can be output centrally. Box Header Connector,Dual Row R-Type Box Header Connector,Box Header Straight Elevator Connector,Smt Box Header 2.0Mm Connector Dongguan Yangyue Metal Technology Co., Ltd , https://www.yyconnector.com