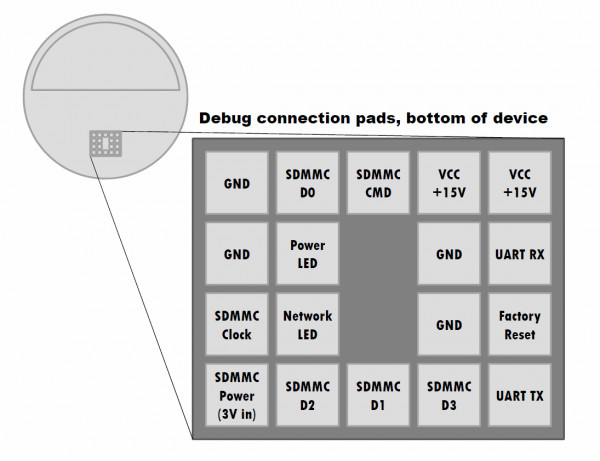
Due to the need for interaction, Amazon Echo is always listening to people, so it is also easy to be paranoid as a listener. Recently, a security researcher's experiment tells us that there is no clear security line between the cute speakers and the evil monitor. With only a few minutes of operation, a hacker can convert Echo to an eavesdropping microphone without leaving any traces. A report by wired introduced this experiment and finally gave everyone the ultimate solution. British security researcher Mark Barnes detailed the malware installation techniques in Amazon Echo in his lab's blog. Practice has proven that his code can secretly transmit audio to his server. This technology first needs to be hand-in-hand with Echo's physical products, and it will only work for Echo sold before 2017. Barnes warns that for those products sold before 2017, this loophole cannot be fixed by software, and the modified Echo has no appearance flaws. Although the emergence of this technology is not enough to make every Echo user scared, but it does point out the security issues that exist in Echo, with the increase in sales, people will carry Echo out. More and more Echos are left in hotel rooms or offices. Users cannot keep an eye on it and leave opportunities for people with bad intentions. Retrofit Echo "We have demonstrated a technology of root Echo and then turned it into a bug," said Barnes, who is a security researcher at the MWR lab in Basingstoke, UK. His blog describes how he installs his own malware on Echo by first creating a "root shell" that allows him to connect to blackened Echo over the Internet, and finally "remotely monitor" Ehco, who is recording continuously. This method exploits the hardware security holes left by Echo sold before 2017. The removal of Echo's rubber base reveals some of the underlying metal pads. Their role is to link internal hardware. They should be used to test and fix errors before they are sold. For example, one of the metal disks can read data from the SD card. Echo metal pad distribution So Barnes connected two small metal plates by welding, one connected to his laptop and the other to an SD card reader. He then used Amazon's own features to load his modified Echo “boot loader†from the SD card. This program is rooted in hardware devices that can wake up the operating system themselves, can also turn off the operating system's authentication measures, and allow him to install software on Echo. Although welding takes several hours and there is physical evidence, the wires extending from the connections will be distributed everywhere, but Barnes said that as the development progresses, plugging in special devices can directly connect these. Pads to easily achieve the same effect in minutes. In fact, an early paper by a research team at the Castle Military Academy in South Carolina also corroborates Barnes's statement, suggesting that hackers can use 3D printed devices to connect to pads. Barnes explained: "As long as this tiny rubber bottom, you can directly connect these pads. You can make a plug-in device, so you do not have welding, and there will be no obvious operating marks." After the software he wrote had acquired the ability to connect to Echo, Barnes wrote a simple script that controlled the microphone and transmitted the audio to any given remote computer. He pointed out that such software can easily perform other evil functions, such as using it as an access point to attack other parts of the network, stealing users' Amazon accounts, or installing other ransomware. Barnes said: "You can use it to do whatever you want, really." Simple trick Amazon has fixed this security flaw in Echo that Barnes discovered in the latest version. Barnes said that Amazon has eliminated this possibility on hardware products. When WIRED asked Amazon about the matter, Amazon wrote in a statement: "In order to ensure product safety, we recommend that customers purchase Amazon-made equipment from Amazon or a trusted retailer and maintain software updates. †Barnes agrees that his experiment is mainly a warning to those who bought Echo from outside the Amazon. For example, some second-hand Echo may have been modified. However, he also pointed out that the software update is unable to save the early Echo, because the problem lies in the loopholes in the hardware. He said that people should consider using Echo's security risks in public places or semi-public places. For example, Wynn Las Vegas plans to place Echo in each room. Barnes said: "In this case, you simply can not know who has connected Echo. "Maybe the hotel's former guests installed something inside, or cleaners, who are all suspect. The idea of ​​turning indoor smart service devices into spyware isn’t just about paranoia: Wikileaks’ documents show that the CIA has developed similar physical access technologies designed to turn Samsung’s smart TVs into eavesdropping devices. . For those who fear that Echo has been transformed, Barnes points out that Amazon still has a hand. Echo has a mute button and is Echo's switch. It is a malware that cannot be bypassed. He recommended this method: "If this button is closed, there is no way to restart the software," he said. So this is his trick: "One pass is the spirit." Pcb Control Board Assembly,Circuit Board,Printed Circuit Board,Pcb Assembly Full Industrial CO.,ltd. , https://www.iotaindustrial.com